Thoughts and opinions on all things related to IT and Network Security
Thursday, July 2, 2009
Security 101 : Understanding Antivirus Software
The purpose of anti-virus software is to try and identify and block viruses, Trojans and other malicious software (often referred to as malware) before it can infect your computer and to remove any infections that may be present at the point that anti-virus software is installed.
Different Antivirus packages take slightly different approaches to detecting an infection but generally speaking they usually scan the computer for patterns or "signatures" associated with known viruses. Some anti-virus packages also offer "heuristic" scanning which attempts to recognise the characteristics of malware even if the package does not have a specific signature for the virus, the functionality is included as there is often a short time lag between a virus appearing and antivirus vendors releasing new signatures for their products. Most modern packages will scan the computer's memory and files held of the computer's hard drive or removable storage; typically files will be scanned either a part of a scheduled scan, a manual scan or when they are accessed by the user.
What happens when antivirus software detects a virus?
The response to an infection varies from package to package but typically the software will attempt to clean the file (remove the virus); if it is unable to clean the file it will offer you an option to quarantine the file (move it to a special directory for infected files) or delete the file. Depending on the package and configuration you may be prompted to confirm some or all of these actions; you should ensure that you are familiar with how your antivirus software responds to particular situations.
Best Practice for Using Antivirus Software
Once you have installed antivirus software you need to ensure that the virus signatures are kept up to date. Most modern antivirus packages include some kind of automatic update function that will retrieve updates from the company providing the software. The detail of how this is achieved will vary from package to package but the end result is the same. It should be noted that most antivirus software companies charge an annual subscription for these updates, so it is important to keep your subscription in good standing so that you continue to receive the updates; most antivirus software will warn you if your subscription expires. If your antivirus software requires manual updates make sure that you update the virus signatures on a regular basis (at least once a week).
Immediately after installing your antivirus software you should run a complete system scan. This will enable you to detect any infections that may have been present prior to the installation of the antivirus software. Most packages prompt the user to perform a complete system scan after installation but, in the event that your package does not, make sure that you take this step.
Ensure that you enable file access scanning (it is usually enabled by default), this will cause your antivirus package to scan files as they are accessed and report on any infections.
Configure a scheduled scan of your PC for once a week; depending on the performance of you PC your computer may become unusable during the scan and you may want to schedule the scan for a time when you are not using the computer.
For removable media such as CD-Roms, DVDs, USB memory sticks etc., consider disabling auto-run behaviour (where you computer will attempt to automatically run software on the removable media) and manually scan the removable media before you open any files.
When opening email attachments or downloading files from web sites, save them to you PC before opening them to ensure that your antivirus software has an opportunity to scan the file.
Tuesday, June 30, 2009
Mozilla Foundation releases Firefox 3.5
Monday, June 29, 2009
Adobe Shockwave - New Version Addresses Security Vulnerability
All previous versions of Shockwave are affected by the vulnerability and Adobe recommend that all users update to the latest release.
Finjan Provides Free Browser Plug-In for Secure Browsing
The Finjan add-on, unlike other similar applications, actually scans the linked site for potentially dangerous content, rather than relying on details of a site's reputation. This has the potential to be both good and bad in that it does not rely on external services or databases that need to be kept up to date but it also has the potential to generate either false positives or negatives. My initial testing to date suggests that it tends to miss some of the more obvious sites that should be flagged as potentially dangerous; but I am going to continue to trial it and see what it achieves in the longer term.
If you want to give it a try Finjan SecureBrowsing can be downloaded here.
Friday, June 26, 2009
Increase in spam, phishing and malware attacks linked to the deaths of Michael Jackson and Farah Fawcett
It is worth remembering the best practice guidelines for dealing with unsolicited mail as follows:
- Do not follow web links received in unsolicited email messages
- Make sure that your anti-virus software is up to date
Security 101 - Using Wireless Hotspots - New White Paper
Firstly, let’s define what we mean by a wireless hotspot. A wireless hotspot is a wireless service in a public area such as a hotel, restaurant or coffee shop which is either provided by an external service provider or by the establishment itself. Wireless hotspots are available either as a “paid for” service or in some cases are provided free by the establishment.
Using a wireless hotspot can be risky in certain circumstances, but what are the risks and how can you mitigate them.
View the white paper here
Microsoft Release Trial Version of Free Anti-virus
In the past Microsoft has been criticised for not providing security software with Windows. It's first attempt, called Windows Live OneCar, did not attract many customers and will be discontinued. Microsoft is hoping that MSE, available as a free download, will prove more popular. Microsoft has said it will provide automatic updates.
It should be noted that MSE only provides protection against malware and does not include the more sophisticated components included in commercial rivals such as firewall, web filtering and parental controls.
Thursday, June 25, 2009
UK has cyber-attack capability
It has long been suspected that a number of nations have engaged in cyber attacks; often to gain commercial advantage for home grown companies. Lord West has said that the UK does not engage in industrial espionage but refused to be drawn of whether cyber attacks were used for military or diplomatic purposes.
Lord West stated that the UK had recruited a team of former hackers for its new Cyber Security Operations Centre, based at GCHQ.
Civil liberties campaigners are concerned as to whether these developments will lead to an extension of the government’s invasive counter-terrorism powers although the government has stated that the unit will not “be used to spy on ordinary people.”
Adobe Shockwave Player Vulnerability
Sunday, June 21, 2009
Google Launch Anti-Malvertising Service
Google's service searches a range of independent websites from other companies, service providers and security specialists dealing with the distribution of malware or advertising for specific terms, domain name etc; the more hits the more likely it is that there is something wrong. This is, however, only intended as an indication that further research is required before coming to a decision.
More information can be found at www.anti-malvertising.com.
Friday, June 19, 2009
Enabling Encryption on Gmail
1. Log into your Gmail account in the normal way and click on "Settings" at the top of the screen; this will display Gmail's settings.
2. Select the "General" tab (if it is not already selected) and scroll to the bottom of the screen. You are looking the "Browser Connection" options show in the picture below (click on the picture to see a larger version).
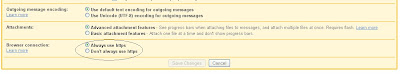
3. Select "Always use HTTPS" and then click "Save Changes". Your Gmail account will now use HTTPS for all communications, reducing the possibilities for "man in the middle" type attacks.
Our recommendation is always to use HTTPS although this is particularly important if you are planning on using insecure Internet connections such a public Wi-Fi or Internet cafes.
Google Tackled Over Gmail Security
A key concern of the signatories is that, as more of us used insecure Internet access – such as public wireless networks – there is a risk of sessions being hijacked by criminals who could then impersonate the genuine user.
Google currently only protects the log in process as user’s sign in, as soon as the sign in process has completed encryption is turned off. It is possible to force Gmail, Google Docs and Calendar into using encryption all the time but the option is difficult to find and many users simply retain the default settings. Every web mail provider currently faces the same problem.
Parcelforce Leak Personal Data
Customer using Parcelforce Worldwide to send packages are given a reference number, which allows them to track the progress of their delivery but when this reference number was entered the ParcelForce tracking system displayed details of unrelated deliveries, including some parcels that had already been delivered.
ParcelForce have corrected the problem, which occurred after upgrade work on Wednesday night and have apologized to customers.
Security 101 - Understanding Firewalls
Firewalls come in two forms: hardware and software. Hardware firewalls are external devices that are normally positioned between your computer or network and your Internet connection. In the case of home users, your Internet Service Provider may have provided a device described as a “router” that incorporates some firewall functionality.
Hardware Based Firewalls
Hardware based firewalls are particularly good for protecting multiple computers but also offer a high degree of protection for a single computer. If you only have a single computer behind the firewall or you can be certain that all of the other computers on the network are up to date on patches and a free from malicious software you may not need the additional protection that can be provided by installing a software based firewall.
Hardware firewalls have the advantage of being separate devices running their own operating systems and as such provide an additional line of defence against attacks. The main drawback of hardware based firewalls is cost.
Software Based Firewalls
Some operating systems provide built in firewall functionality; if the operating system that you are using includes this functionality you should consider enabling it. If your operating system does not provide this functionality there are a number of free, shareware and commercial offerings available. We recommend that firewall (and other security software) is only ever installed from a CD/DVD obtained from a trusted source as this mitigates the risks associated with installing software downloaded from the Internet. If you do want to install security software from the Internet make sure it is from a reputable, secure web site.
Although, it is possible to rely on a software based firewall alone, this is not recommended as having the firewall on the same computer that you are trying to protect limits the firewall’s ability to catch malicious traffic before it enters your system.
What is the best approach?
The best possible approach is to utilize a hardware firewall between your network and the Internet and install (or enable) software based firewalls on all the computers on your network as this will mitigate the effects of attack by external parties and also provide a level of protection against viruses, worms or other malicious software spreading throughout your own network.
Configuration Options
Most commercial firewall products will have a configuration that is acceptable secure for most users but, since each firewall is different, you’ll need to read and understand the documentation that is provided with the firewall to understand whether its default settings are sufficient for your needs.
Be Vigilant
The key thing to remember is not to be lulled into a false sense of security. While firewalls can limit the possibilities for external attacks and software-based firewalls can provide a degree of protection against malicious software spreading throughout your network, firewall provide little or no protection against malicious software that spreads by email (by tricking you into to clicking on attachments) or compromises web sites. Even if you have firewalls installed you should still make sure that your anti-virus software is up to date and that you exercise caution in the websites that you visit.
Thursday, June 18, 2009
Windows 7 Security Hole Still Open
The purpose of UAC is to guard against malware - it warns the user when applications try to make changes to the computer but "proof of concept" code has been created that can remotely disable UAC without informing the user that this happened. Microsoft have so far started that this is a feature that has been included by design and, therefore, will not be fixed.
Microsoft Optical Desktop 1000 and 2000 keyboard vulnerabilities
Currently only Microsoft's wireless keyboards transmitting on the 27 Mhz band are vulnerable; Bluetooth keyboards are not at risk.
The vulnerabilities in Microsoft keyoboards have been known about since December 2007 but as yet there are no indications that Microsoft has taken steps to mitigate the them.
If you want to use a wireless keyboard the answer, for now at least is to use a Bluetooth device otherwise use a wired keyboard.
Your Computer Might be Traded Online - Without Your Knowledge
Golden Cash also provides an exploit tool kit for infecting PCs and manipulating websites. Finjan's report suggests that this platform represents a highly lucrative system. See Finjan's report here for more details.
New web server attack
The HTTP protocol allows clients to split the data from a GET or POST request over a number of HTTP queries; depending on the server configuration, the first such request can cause the server to allocate a large amount of resources for the response while waiting for the rest of the request. The web servers that are vulerable to this type of attack are those that implement strategies to avoid system overloads by, for example, limiting the number of simulataneous HTTP queries. These include Apache HTTP server, DHTTPD, GoAhead Web Server and Squid, but not Microsoft IIS or Light HTTPd. The basic concept behind this new attack is similar to the half-open TCP connections attacks that have been seen in the past, except that this attack generally only affects the HTTP component of the server and other services are largely unaffected.
There are a number of ways to defend against this attack; web servers could be protected using load balancers and web application firewalls that only forward complete HTTP requests to the server or the reducing the time out for HTTP requests.
Apple release iPhone OS 3.0
Wednesday, June 17, 2009
Six Ways to Protect Your Wireless Network
Most wireless LAN hardware is incredibly easy to set up and, in the case of hardware supplied by broadband providers, is often supplied pre-configured. However, it is worth checking the security configuration of your wireless LAN router; here are some simple things you can do to protect your wireless network.
Secure the administration interface. Wireless routers generally have an administrator password that must be entered before the configuration can be changed. Most devices will be preconfigured with a default administrator password and some devices will have no password at all. You should always ensure that an administration password is configured or, if the device has a default password, change it. If you leave the device with no password or with the password set to a default value you run the risk of the device being reconfigured without your knowledge; either by somebody who has managed to attach to your network or by malware that you have inadvertently downloaded.
Use WPA encryption instead of WEP. 802.11’s WEP (Wired Equivalent Privacy) encryption has weaknesses that make is relatively easy to crack the encryption and access the wireless network. A better encryption standard is WPA (Wi-Fi Protected Access) which provides much better protection and is easier to use. WPA support is built into almost all modern wireless hardware and operating systems. WPA2 is a more recent version of the standard which provides even stronger encryption.
It is possible that you may have some devices that do not support WPA (often devices such as media players, PDAs etc). In this situation it is tempted to turn encryption off completely but this really will leave you wide open to attack. WEP encryption, for all its flaws, is better than nothing and therefore should be used where you have devices that do not support WPA. If you do use WEP make sure that you do not use an easy to guess encryption key. You should also consider changing the WEP encryption key at least once a week.
Don’t broadcast the SSID. Most wireless access points and wireless routers continuously broadcast the wireless network’s name, this is also called the Service Set Identifier or SSID. The purpose of this is to make it easy to configure wireless networks as wireless devices will be able to identify the wireless networks that are available. However, it also advertises the presence of your wireless network to any wireless systems in range. Turning of SSID broadcast will make your wireless network invisible to your neighbours and the casual intruder but it will still be visible to anybody with a wireless network sniffer.
Use MAC filtering. The MAC address is a hardware address associated with a network adaptor and, unlike and IP address, is globally unique to that adaptor. By using MAC filtering on your wireless access point or router you can control the specific devices that are permitted to connect to it. MAC addresses can be spoofed by somebody with sufficient knowledge, so this does not provide an absolute guarantee of security but it does give the attacker another hurdle to jump.
Disable remote administration. Many wireless LAN routers can be administered remotely from the Internet. You should only every use this feature if you are also able to define a specific IP addresses or a limited range of IP addresses that are able to administer the router. If you are not able to do this anyone, anywhere could potentially access your router. Unless you particularly need this feature it is best to disable it; most wireless LAN routers disable this feature by default but it is always worth checking.
Reduce the Wireless LAN transmitter power. This feature does not exist on all wireless LAN routers and access points, but some will allow you to decrease the power of the transmitter thereby reducing the range of the signal. It is usually impossible to fine-tune the signal to the point where it does not leak outside your premises but you can limit how far the signal reaches thus reducing the opportunity for people outside your premesis to access your wireless LAN.
Eye Chart Test for Conficker
Conficker (also known as Downadup, Kido) blocks access to over 100 anti-virus and security websites. If you are blocked from loading the remote images the first row of the table (popular anti-virus and security web sites) but not blocked from loading the remote images in the second row (alternative operating systems) it is an indication that your computer may be affected by Conficker of some other malware.
The Conficker Eye Chart can be accessed here.
Tuesday, June 16, 2009
Apple Releases Java Updates for Mac OS X 10.4 and 10.5
Monday, June 15, 2009
New malware for Mac OS X
Security experts have discovered two new forms of MacOS X malware both of which were foiund on popular pornographic websites. Historically, the MacOS platform has had very little in the way of virus and trojans; but attacks against the Mac platform have been increasing.
The small amount of malware in circulation for the Mac platform has made some Mac owners complacent; Mac owners are less likely to running antivirus software, for example. This complacency has not been helped by Apple's approach to marketing.
Sunday, June 14, 2009
Scareware, beware!
In its latest update, Microsoft has added code that detects and deletes the widespread Internet Antivirus Pro family of fake security programs. These programs, often referred to as scareware, are becoming more and more popular with high tech criminals. It is estimated that there were more than 9,000 bogus anti-malware programs in circulation in December 2008.
Recently the US government has moved to shut down some of the companies that have been peddling programs that falsely claim to find malcious software on PCs and then charge for the non-existant threats to be removed. As well as claiming to remove non-existant threats, the Internet Antivirus Pro software contains a password stealer that grabs login details.Microsoft set to give away anti-virus software
Thursday, June 11, 2009
The nice things about standards ....
ISO/IEC 27001:2005
The ISO/IEC 27001:2005 standard covers all types of organisations and specifies the requirements for implementing, operating, monitoring, reviewing, maintaining and improving a documented Information Security Management System (ISMS) and relates this to the organisation's overall business risks.
ISO/IEC 20000:2005
This standard was developed to reflect the best practice guidance contained within the Information Technology Infrastructure Library (ITIL) framework. It consists of two part: Specification for IT Service Management and code of practice for service management. ITIL enables organisations to define a model to manage their IT operations covering areas such as service delivery, relationship management, resolution process, control processes, release processes, changed services and service management.
ISO/IEC 18028:2006
This was developed to define a standard security architecture that describes a framework to support the planning, design and implementation of network security. This standard had major contributions from the ITU X.805 standard.
PCI DSS 1.1:2006
The Payment Card Industry Data Security Standard (PCI-DSS) includes requirements for security management, policies, procedures, network architecture, software design and other critical measures. It is desgined to help reduce the frequency and impact of security incidents in the processing of payment cards. PCI-DSS is appliable to any oragnisation that is processing card payments.
This is a brief review of four major security standards and their relevance to different types of organisation.
Friday, April 10, 2009
Conficker - the dog that hasn't barked ... yet!
Gregory: "Is there any other point to which you would wish to draw my attention?"
Holmes: "To the curious incident of the dog in the night-time."
Gregory: "The dog did nothing in the night-time."
Holmes: "That was the curious incident."
There was much speculation in the media about what the Conficker botnet would do on the 1st of April and, as with previous virus scares (Michelangelo, CIH, SoBig etc) it turned out to be more about hype than reality. The Conficker botnet remains dormant … so far.
The main activity in the run up to the supposed activation date of the first of April was a huge increase in the number of rogue security tools masquerading a Conficker clean-up packages. The botnet itself has yet to do anything but the act of spreading has already caused problems and claimed a number of high profile victims include the UK Ministry of Defence.
Conficker started spreading in November 2008 and, like many such worms, it uses a variety of techniques to spread including exploiting Windows vulnerabilities and spreading across network shares. Conficker can also spread using removable media such as USB memory sticks.
Earlier versions include a type of peer-to-peer functionality, this means that computers infected by this version of Conficker can communicate amongst themselves without needing to “call home” to a central server or servers.
Some versions call home to 250 different domains on a daily basis to check for updates. On Wedneday 1st April the latest version of Conficker began calling home to a sample of 500 out of 50,000 domains on a daily basis.
While Conficker hasn’t done anything yet it is a very real possibility that it could in the near future. So should you be panicking, no … as long as you keep your anti-virus package up to date as most up to date anti-virus programs will have no trouble detecting Conficker.
A good FAQ can be found on the F-Secure website http://www.f-secure.com/weblog/archives/00001636.html.
Friday, March 27, 2009
So ... What on earth is a Botnet?
A Botnet is a network of computers that have been infected and are under the control of a hacker or group of hackers. Once they have computers under their control the hackers can use them to propagate viruses, send spam, launch attacks against web sites (distributed denial of service attacks or DDos) or any number of other suspect activities. Criminal gangs have even been known to “rent” their Botnets to other criminals. This is what occured during the recent Botnet experiment by the BBC http://itnetworksecurity.blogspot.com/2009/03/botnets-very-real-threat.html (not that I am comparing the BBC to criminals, you understand).
Botnets can consist of many thousands of compromised computers, with this number of machines under their control the people behind the Botnets can cause all sorts of chaos including Distributed Denial of Service (DDos) attacks against corporate web sites. Botnets are being used by criminal gangs to extort money – sending messages to companies threatening to take their website down unless payment is forthcoming.
One technique that is used in the fight against Botnets is called a honeypot. The idea of a honeypot is to provide an unprotected machine or set of machines and examine how attackers infiltrate the systems. A great site to read up on this topic more is The Honeynet Project (http://project.honeynet.org) which describes its own site's objective as "To learn the tools, tactics and motives involved in computer and network attacks, and share the lessons learned."
Nine Steps to Securing Your Computer
- Always keep backups of important information and keep them in a safe place. It is better to store them away from your home, if at all possible as this will give you additional protection against fire, theft etc.
- Update and patch your operating system, browser and any software frequently. If auto update options are available, use them.
- Make sure that you have antivirus/anti-malware software installed, that it is up-to-date and has the latest patterns installed. If it has an auto-update mechanism, ensure that it is enabled.
- Install a personal firewall. Many home routers provide some kind of firewall functionality but it is always worth having the additional protection offered by a personal firewall. Many home user security packages (e.g. Norton Internet Security) include firewall functions or you can opt for a separate firewall such as ZoneAlarm.
- Check the settings in your Internet browsers. Active-X and Javascript are used by hackers to install malicious software (“Malware”) on computers. Internet Explorer offers a number of “zones” for grouping sites, by default everything is in the Internet zone. Set the security level of the Internet zone to high. Internet Explorer also offers a trusted sites zone for sites that you trust, set the security level in this zone to medium.
- Do not open unknown email attachments from unknown senders and be extremely suspicious of attachments from known senders that seem out of character for the sender. Many viruses and other pieces of Malware spread by compromising email clients and sending themselves to people in the address book.
- Do not run programs of unknown origin as they can contain malware even if they appear to do something harmless. Resist the temptation to forward such programs on to friends, family and colleagues because they are funny or interesting. This is another mechanism used by malware authors to spread their programs.
- Disable the Windows “hidden extension” feature. By default Windows will hide the file extensions of known file types. This option should be turned off and you will be more able to see any unusual file extensions that may be there.
- Consider disconnecting your computer from the network and/or turning it off when you are not using it.
You should also consider making a boot or emergency disk for use in case or computer is compromised by malware.
Fundamentally, you can never be too vigilant and the simple steps discussed above may prevent you falling foul of a damaging attack.
Wednesday, March 18, 2009
Avoiding Pharming and DNS Exploits
In essence it was a variation on the idea of “pharming” where a hacker attempts to redirect traffic legimate website traffic to a different, fraudulent, website – the most common use of this exploit is to re-direct traffic destined for on-line financial site in order to harvest user names, passwords and other security credentials. There are a number of ways this type of attack can be executed.
The first, and simplest method is to compromise the hosts file on the user’s PC. The hosts file is a remnant of ARPANET, the predecessor of the Internet, which did not have a domain name system for resolving network names. Instead each node held its own records of other nodes that it needed to know about and this is what is contained in the hosts file. An entry contained in the hosts file will override the need to look up an address using the domain name system.
In order to execute an attack the hacker needs to modify the host file; something which can be achieved by enticing the user to download a small piece of malware to their computer – this malware would then modify the hosts file with the name of the site they wished to direct and the bogus IP address that they wished to redirect it to.
The second way of executing a pharming attack is to use a technique call DNS cache poisoning – this is where the hacker compromises a DNS server by exploiting a flaw in the DNS server software and cause the DNS server to accept bogus information. By doing this the DNS server will then provide an incorrect IP address for a given name and direct users to the attacker’s web site.
The third way uses malicious code to reconfigure the DNS settings of a user’s home router, this is also called a “Drive by” pharming attack. If you look at the configuration of your home router somewhere in its configuration you will usually find references to primary and secondary DNS servers – these parameters are usually set to whatever your ISP provides but, even when your ISP has provided the configuration, it is possible to change these settings.
In this attack, the hacker changes these DNS settings so that any attempt to resolve names is not sent to the ISP’s DNS server but to a DNS server controlled by the hacker. Thus, the hacker is able to provide whatever address he chooses and redirect the traffic to another server under his control. Thus an attempt to access the Natwest web site (www.natwest.com) could result in the user being redirected to a bogus server offering web pages that look superficially like the genuine site – allowing the hacker to collect online banking credentials.
This attack requires the user to be tricked into downloading some malware to their PC – either via Javascript embedded into an email or via a compromised web site. In many cases it will also require the administrative user name and password for the home router, although many users do not change the default and a quick session with a search engine will usually reveal the default username and password for most popular home routers. Scarily, there are some home routers out there that allow the username/password validation for administrative access to be bypassed.
So, what can you do to protect yourself – here are some simple tips.
Does the web site displayed in your browser look genuine? If it is something sensitive like an online banking site, is it using HTTPS (the padlock symbol is most browsers).
If the site is using HTTPS did you get a certificate warning? If you get a certificate warning you should never, ever proceed.
Does the site seem to be asking for too much information? Most online financial institutions have a user name, password and several pieces of memorable information. If the site that you have connected to wants you to provide all of this information in one hit then it is not the genuine article. Likewise, if the site you have connected to is asking you to type your complete password when you would normal select specified characters from a drop down list or click keys on an on screen keyboard, it is not the genuine article either.
Change the default administrative user name and/or password on your home router.
Good luck – and stay secure.
Saturday, March 14, 2009
BotNets – a very real threat
Thursday, March 12, 2009
Endpoint Security II - Removable Media
Many of the recent data leaks in the public sector have been as a result of problems with removable media – from the well publicized case of child benefit records in the UK being sent unencrypted on CDs through an insecure mail service to any number of cases where USB memory sticks have been lost.
The trouble with removable media is that is so convenient – how many times have you used a USB memory stick to transport information without thinking about how that information is protected or the consequences of losing that information. A particular issue with USB memory sticks is that they are quite small, while this does make them convenient it also makes them very easy to lose.
There are two issues – one is user training about appropriate use of removable media –simply there is some information that is so confidential that it should never be stored on removable media. This should also be backed up with an enforcement and auditing system.
The second issue is mitigating the effect of losing removable media – this is really the domain of encryption products, if the data is encrypted then the usefulness of the removable media to anybody who does not have the encryption keys is seriously limited.
Wednesday, March 11, 2009
Endpoint Security I – Laptop Security
The portability of laptops makes them inherently vulnerable; they are designed to be portable. Traditionally, people and organizations consider laptop security from the perspective of the financial value of the device but as the cost of laptops has reduced it is likely that the information contained on a laptop’s hard disk is more valuable than the laptop itself.
There are a number of simple measures that can be taken to protect laptops and the information they contain such as not leaving them unattended in public areas or in parked cars (whether on display or not). This is an issue that can be addressed by training, but even the most careful person can make mistakes. So what can be done to protect the data against compromise when a laptop is lost or stolen?
It would be relatively simple to design a system where little or no data is held on the laptop itself; this would require the use of some type of thin client arrangement such as Windows Terminal Services or Citrix where all applications run and all data is held on centrally located servers and the endpoints simply function as a “dumb” terminal that simply provides an interface to the user. The problem with this kind of implementation is that constant connectivity is required to the central data centre(s) hosting the applications.
So, given that most users are going to store some data locally what can be done to prevent this data falling into the wrong hands. The answer is to encrypt some or all of the information held on the local hard drive; there is a wide choice of products available to achieve this; however, some considerations in selecting a product.
Ease of use – the product has to be easy to use and the process of encryption and decryption as transparent as possible to the user. Most people are not technical and if they are provided with something that is difficult to use they will not use it.
Security of the encryption algorithm
Management of encryption keys – it is important that the organization as the ability to manage encryption keys. Under section 53 of the Regulation of Investigatory Powers Act (RIPA)(UK) the police have the powers to demand the decryption of data or the production of decryption keys; it is clearly important that an organization should be able to comply with this requirement.
Security of passwords/encryption keys when held in memory – at some point most encryption systems are going to hold user passwords or encryption keys in dynamic memory. When this occurs there is a risk that a malware program that has infected the laptop could steal this information and provide it to a third party; therefore, any encryption system should provide some method of obscuring or protecting this information while it is held in dynamic memory.
Next time … more on endpoint security, specially looking at removable media.
Tuesday, March 10, 2009
Public Sector Data Leaks
The public sector is being driven by the requirement to aggregate data from many sources into large databases; this increases the attraction to criminals as there is the potential to harvest more data from compromising a single database. Another effect of data aggregation is that it becomes increasingly difficult and costly to “dis-aggregate” the data when sharing it with third parties
This is exactly what happened in well publicized case of the lost child benefit records; the National Audit Office had requested specific “de-personalised” data – internally within HMRC it had been decided that it was too expensive to depersonalize the data in the way requested by the national audit office had requested and, therefore, the complete data was sent; this was only compounded by the fact that the data was sent unencrypted on a CD via an insecure mail service.
As well as the primary effect of this incident (the compromise of people’s personal details), there was a secondary attack where people were targeted with a email offering a £215 tax rebate which redirected them to a malware site.
The bad news is that it is getting worse, in the 12 months to September 2008 there were 12 major incidents in the public sector affecting 29 million records. See http://www.silicon.com/publicsector/0,3800010403,39295167,00.htm for more details.
The government’s response to data has been a working party that produced the following recommendations.
Changes to policy, systems, procedures and controls with the focus on trust, reputational risks, cost avoidance and accountability.
However, the focus is on risk and cost avoidance from a government perspective. In most of these incidents the government bears very little cost or risk. In the case of the HMRC incident the risk was borne by the individuals claiming child benefit (potentially having their bank accounts compromised) and the cost was borne by the banks (the administrative effort in potential losses through fraud, changing account numbers, reissuing cards etc).
Penetration Testing.
Penetration testing is a worthwhile exercise but it assumes that the weakest point is the network perimeter; this would not have prevented any of these incidents occurring.
Encryption of end points.
All of these incidents have occurred because of endpoint vulnerability; the CD, the USB memory stick or the laptop left in a taxi. Clearly the encryption of endpoints is critical in mitigating risk if the endpoint itself is lost or stolen.
Unfortunately, they do not address the real issue – the people in control of the data have no interest in keeping it secure, an effect called externality. The organizations involved do not bear the consequences of their actions – there is no point in fining a public sector organization as it is public money anyway. The only way this issue will be addressed is for the individual employees of these organizations to bear the consequences of their actions – and ultimately this will probably man serious criminal sanctions.